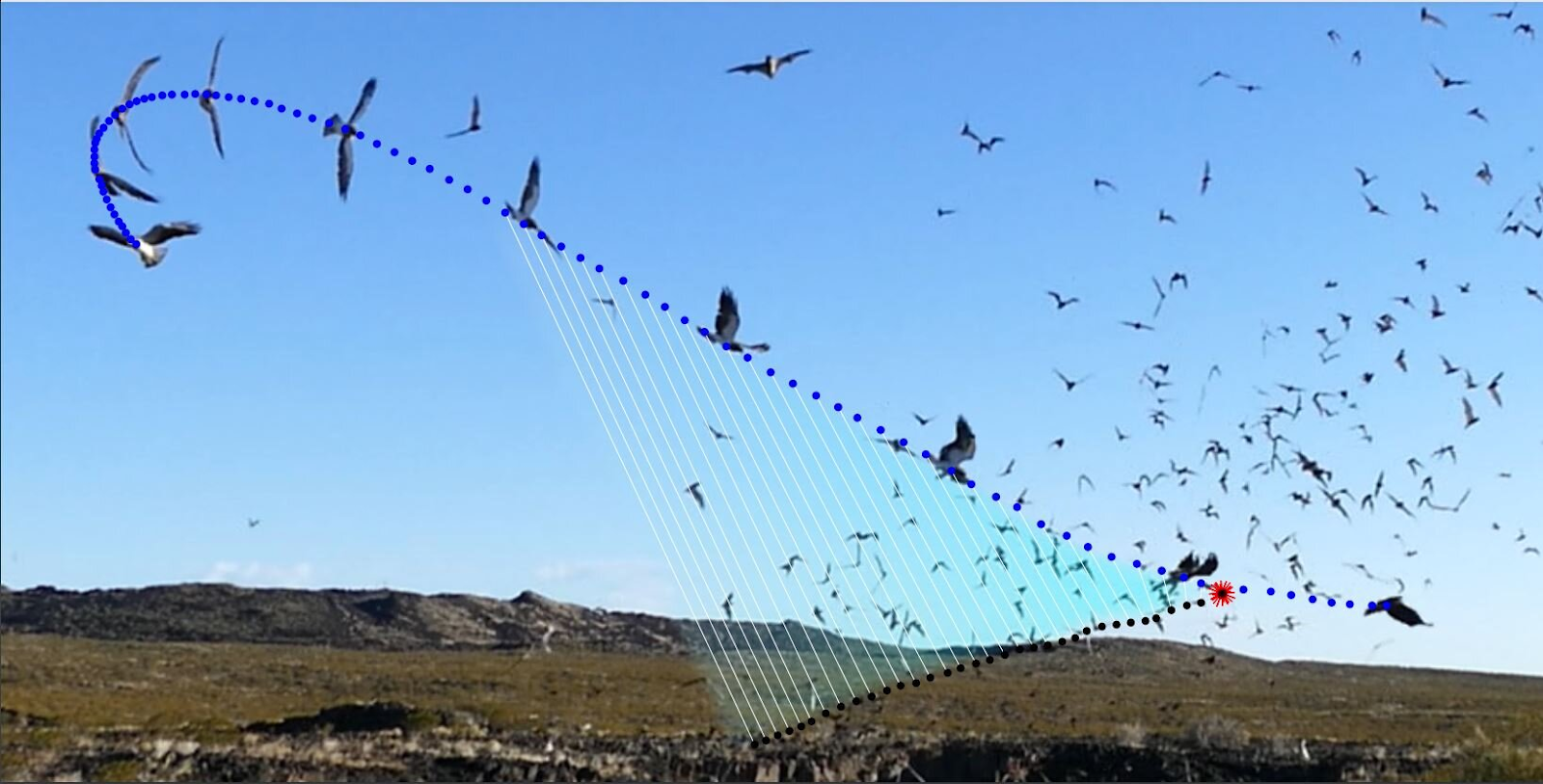
"Composite frame sequence of a Swainson’s hawk attacking swarming Mexican free-tailed bats at a bat cave in New Mexico, USA. The white lines connect the hawk to the bat that it captures, and remain parallel over time showing that the bat remains on a constant bearing. Credit: Caroline Brighton (Oxford Flight Group)"(Phys.com/ Study reveals how hunting hawks home in on prey inside a chaotic swarm)
Many swarming animals, such as insects and birds, use chaos as a shelter. Chaos makes it harder for a predator to pick a single bird or insect from that chaotic flock. Information about how animals such as hawks or dragonflies select targets and attack them makes it possible to create algorithms that are used to select the main movers from a flock of drones.
The prime mover is the drone that goes first. And the secondary drone is the backup tool. That mission is to observe the prime movers. They are forming two- or more-stage hierarchical systems that can make their mission waves.
Flocks of drones imitate nature. They try to create chaos by hiding drones that are higher up in the hierarchy. The drone swarm is a hierarchical network of the entity, in which the main trustees and secondary movers collaborate with their pilots by sharing information across the whole, which is a combination of drones and their controllers.
Drone swarms are powerful tools and in the next-generation military systems, drone swarms are playing a vital role in aiming other weapons and attack against enemies. The drone swarms can use chaos for making the air defense harder to locate the centers of those swarms.
In some visions, the center drones are more sophisticated, made of more expensive components, and equipped with more effective computers and they have sharper sensors than attack drones. And even if all of those drones have similar systems there must be drones that are making sure that the mission is successful.
So there are always prime movers and then the secondary movers that are observing the mission. If the mission is not done, the secondary movers must accomplish that.
Those centers are used to control their hench drones that are equipped with explosives and weapons. The drone swarm can use chaos for making the AA flak harder to detect the drones that are controlling the systems. But there is always a prime mover in those swarms. The prime movers are hard, but possible to detect from the drone swarms.
https://phys.org/news/2022-08-reveals-hawks-home-prey-chaotic.html